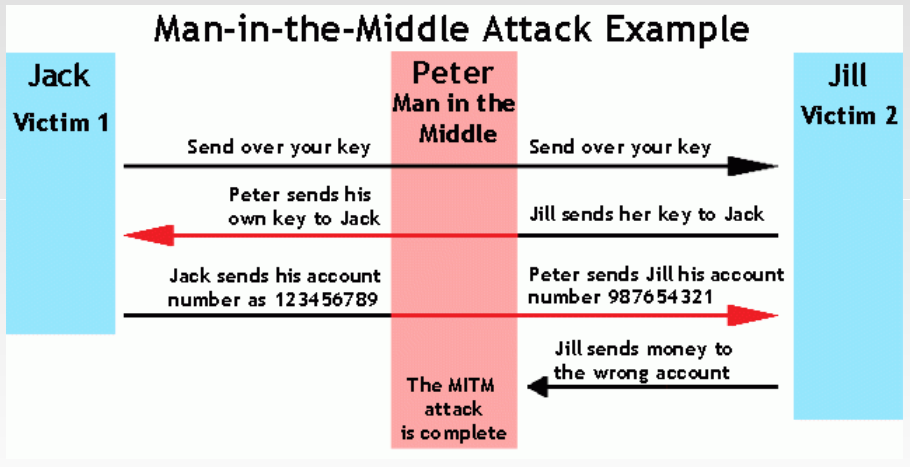
Man In The Middle Attack is also known as Hijack Attack.Here what hacker does is he acts as an inter-mediator between client and server communication.Here client thinks that he has a direct connection with server and shares private information such as passwords,credit card numbers or OTP.
EXAMPLE:
You are connected to you home WI-FI and you are on XYZ.com for an online transaction and you think you are directly connected to the website but there there's an attacker who is acting as a inter-mediator and whatever you are sending it to the server or trying for any transaction the request first goes to the hacker and he can modify as he/she needs and then can send back the request and when the server response back to the request ,the request goes to the hacker first and then he/she forwards it to you.
Mitigation:
- Use a Virtual Private Network (VPN) to encrypt your web traffic. An encrypted VPN severely limits a hacker's ability to read or modify web traffic.
CAM TABLE OVERFLOW ATTACK:
- CAM(Content addressable memory ,refers to dynamic table) is a attack where a Man In The Middle (MITM) send bogus ARP request to the switch.
- Switch will be receiving many ARP request and after which the genuine user MAC address would be removed.
- Once our MAC address is removed and if we send a data from any interface what switch will do is it will first check whether is there any entry with that interface if found it will send the data to corresponding interface but in this case our arp entry would go missing so the switch would broadcast the message to all the ports available
- which will lead to Eavesdropping
Example:
- You are connected to a public network and sharing some confidential data to you peer or office-mate but hacker comes in between and sends bogus ARP request to the switch using commands ,In a second it can send around 10-15 bogus ARP request.
- Our MAC address is vanished because of bogus request so after which if you send any data to your peer or office-mate.
- Switch checks the entry if not found broadcast it after which we lose our data or in other word our confidential data is everyone in our network
Mitigation:
- To configure switch port security and allow maximum number of MAC addresses to 5 or limited according to your requirement
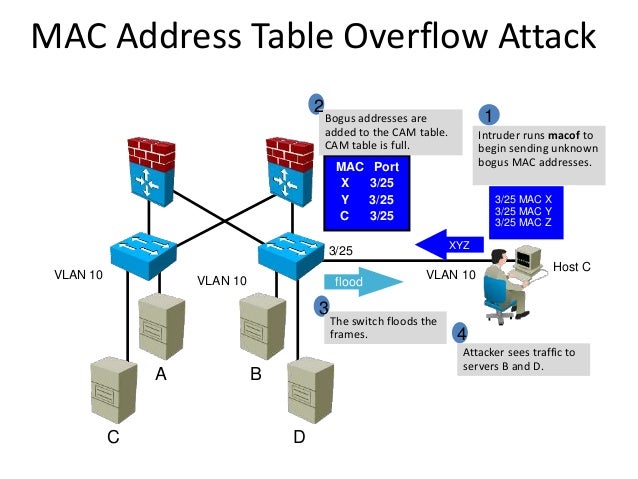
Pic Source: Slideshare
Image explaining MITM:
DNS Spoofing:
- DNS Spoofing is also referred as DNS Cache Poisoning
- DNS Spoofing is an attack where the attacker acts as a Legitimate DNS Server but in real time he is not the legitimate server instead malicious one.
EXAMPLE:
- You are sending a HTTPS/HTTP request to FB.com ,what attacker does is creates a HTML page which is fake page of FB.com and the page would look same as FB.com
- When you connect to FB.com and when you enter the credentials to log-in it goes to the malicious website and now the hacker knows your id and password.

Pic Source: Cyperpunk
Mitigation:
- Monitoring network's traffic is one of the way to stop DNS Spoofing
Thank you for reading :),see you in next blog!



Very informative Anand. Good one, keep it up!
ReplyDeleteRegards,
Dilip Suthar